Halo Security is a fast, easy, and scalable external attack surface management platform that gives security leaders deep visibility into their internet-facing assets.
Traditional vulnerability and risk management solutions were designed for traditional networks. Halo Security takes the attacker’s perspective to help you identify, assess, and monitor the risks across clouds, third-party providers, and organizational silos.





You can't protect assets you don’t know about. Our automated solutions identify and catalog known and unknown domains, hostnames, and IP addresses exposed to the internet.
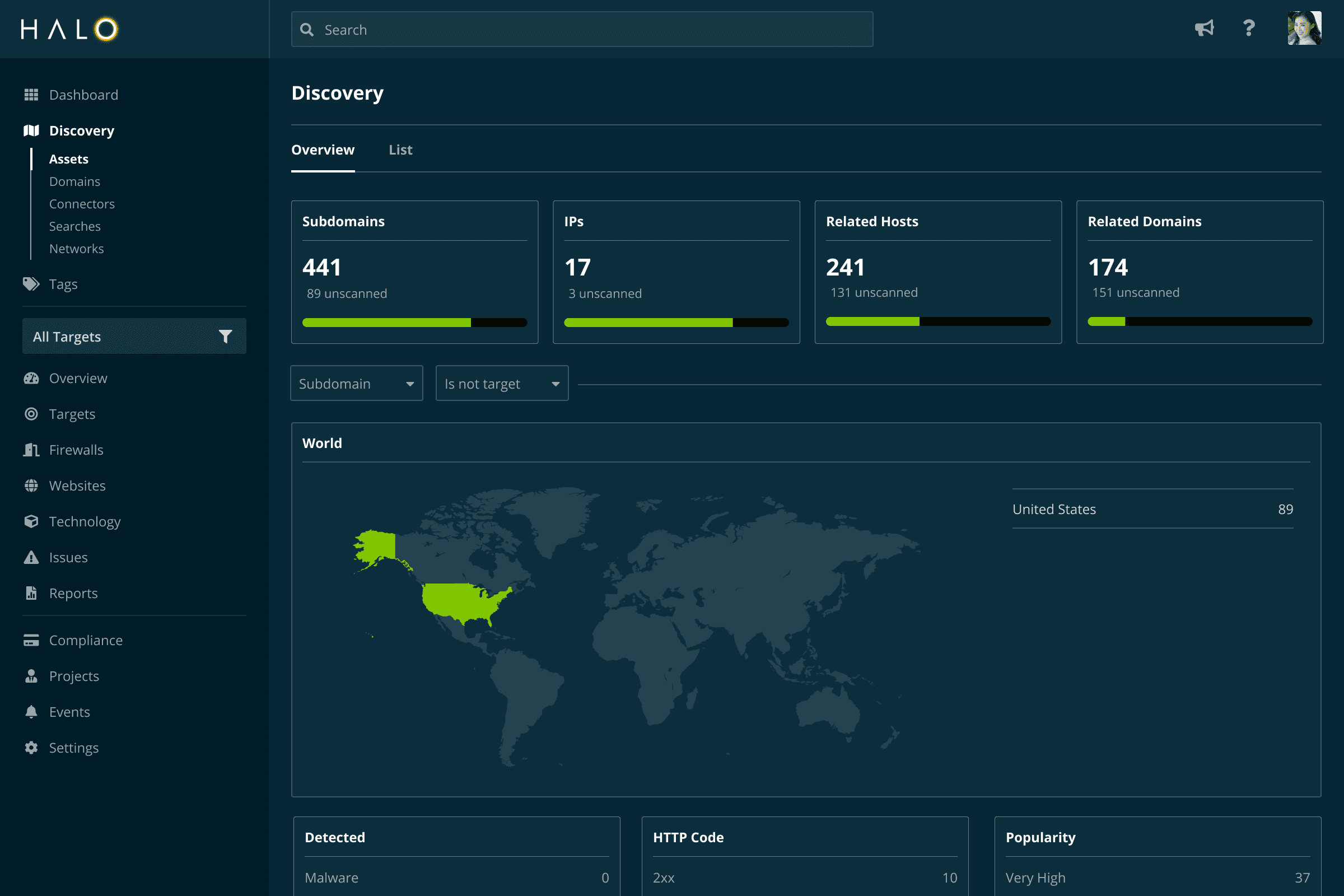
The rich data we collect brings you the context you need to understand what the asset is, what’s running on it, and who’s responsible for it.
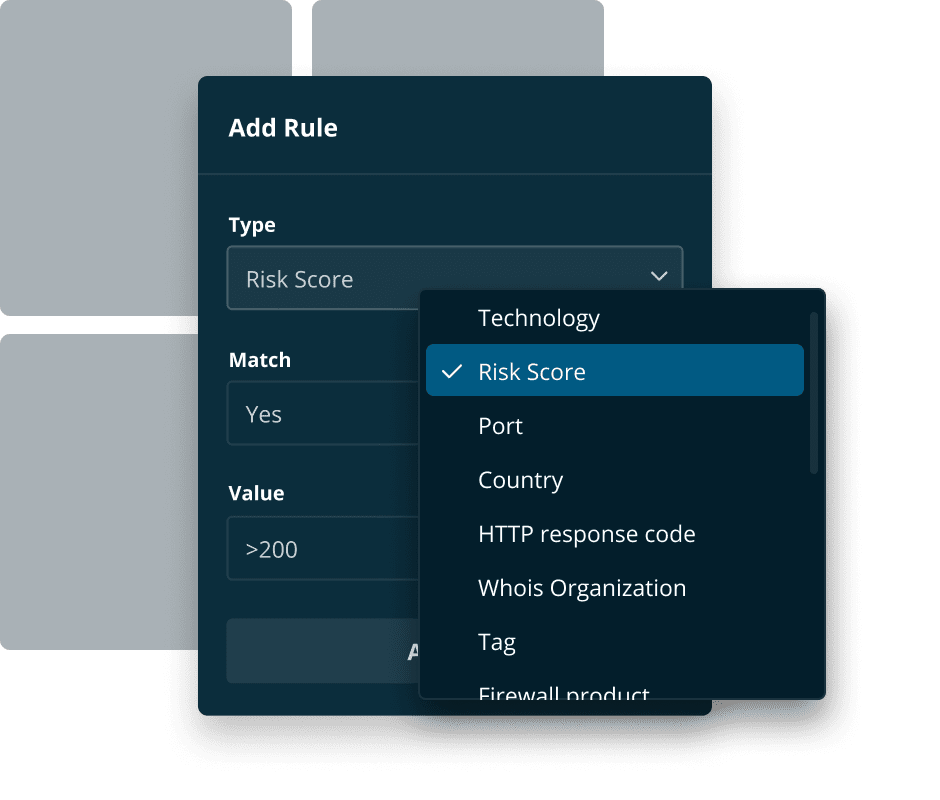
Our agentless vulnerability detection is tuned for internet-facing assets and goes beyond simply detecting known vulnerabilities (CVEs). And yes, we detect those too.
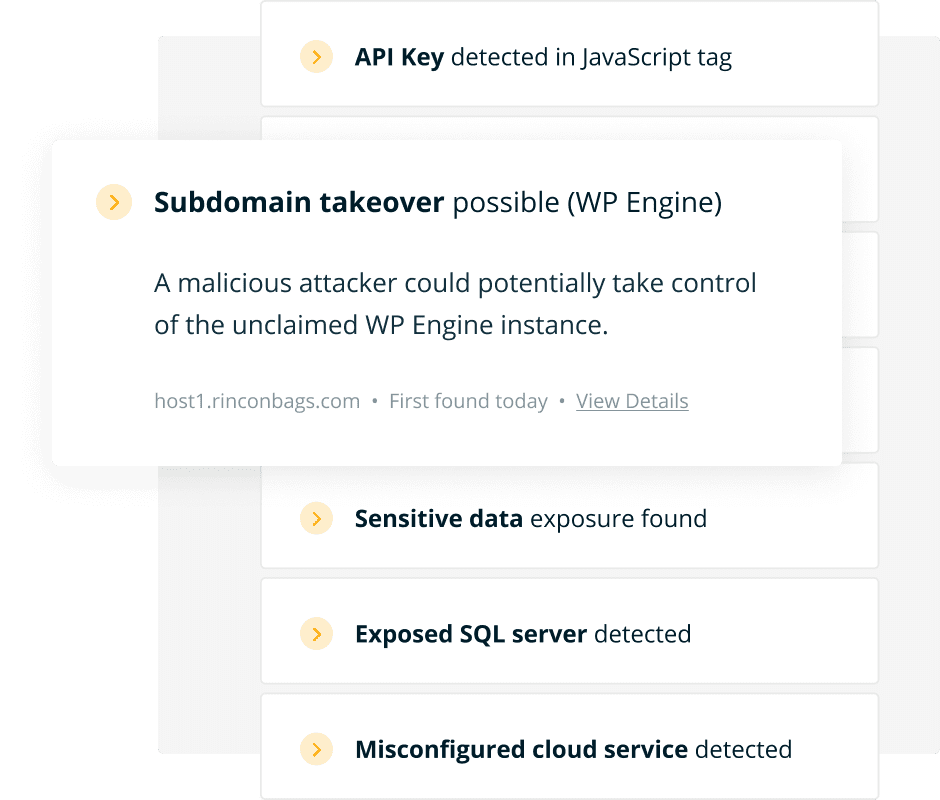
Measure and report on your external risk posture, while prioritizing the issues that matter most.
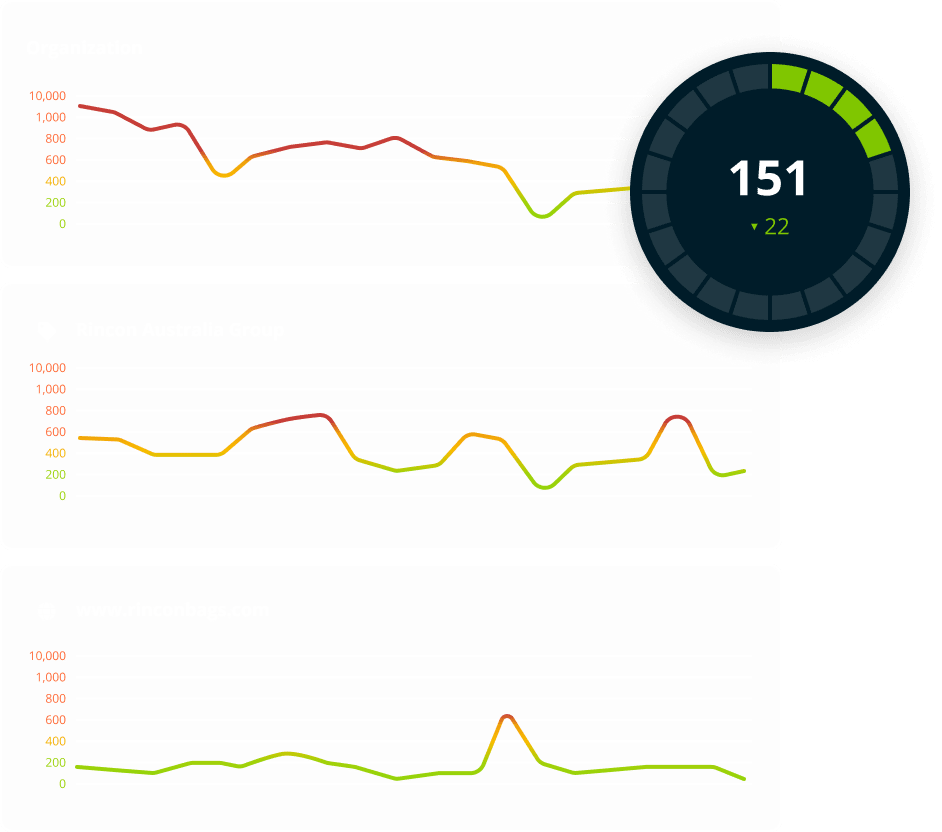
When the next Log4j strikes, you don’t want to be caught running manual exercises to find out if you’re using that software. The Halo Security platform makes it easy to find the most critical insights about your attack surface in seconds.
We offer agentless scanning and single-pane-of-glass visibility out of the box. But we also make it simple to move your data where it makes sense for you.
Continuous vulnerability detection and prioritization helps you efficiently eliminate risks.
With automatic categorization and zero installation, it's easy to measure and evaluate subsidiaries.
Achieve your compliance goals faster with Halo Security, a PCI DSS Approved Scanning Vendor (ASV).
We offer comprehensive vulnerability scanning fine-tuned for internet-facing assets.
Easy-to-use dynamic application security testing (DAST) helps you evaluate custom web applications.
Our integrated manual penetration testing services help discover issues automation can’t find.
We’re a private, woman-owned business founded in 2013. We’re led by ethical hackers and software engineers. Our roots in external risk management stem back to 2001, when our CTO developed one of the first commercial vulnerability scanners.
100% funded by our users.

Per Month
Let us show you a complete picture of your external attack surface. Our agentless, non-invasive technology allows us to bring you actionable insights before you ever see a contract.
Schedule a demo